Join our Mailing list!
Get all the latest news, exclusive deals, and feature updates.
Find answers to common questions about our services, processes, and offerings below. The Phoenix team has compiled this section to help clarify key details and provide quick access to the information you need. If we haven’t answered you question, please contact us at phoenix.security/contact
Application configuration and scanner configuration are available at kb.phoenix.security
Threat
There are many threat actors out there, including nation states, criminal syndicates and enterprises, hacktivists, insiders, and lone wolf actors. These threat actors play on a variety of motivations, including financial gain, political statements, corporate or government espionage, and military advantage.
Vulnerability
Threat actors are able to launch cyber attacks through the exploitation of vulnerabilities. In cybersecurity, these vulnerabilities are fixed with a process, procedure, or technology.
For example, an employee may choose to exploit their familiarity with internal processes, procedures, or technology, such as their knowledge of the following:
Failures in both process and technology could then be exploited by said insider. And of course, there are also a number of vulnerabilities in both hardware and software that can be exploited from the outside, such as unpatched software, unsecured access points, misconfigured systems, and so on.
Consequence
The consequence is the harm caused to an exploited organization by a cyberattack — from loss of sensitive data, to a disruption in a corporate network, to physical electronic damage. Consequences from a cybersecurity incident not only affect the machine or data that was breached, but also affect the company’s customer base, reputation, financial standing, and regulatory good-standing. These can be considered direct and indirect costs.
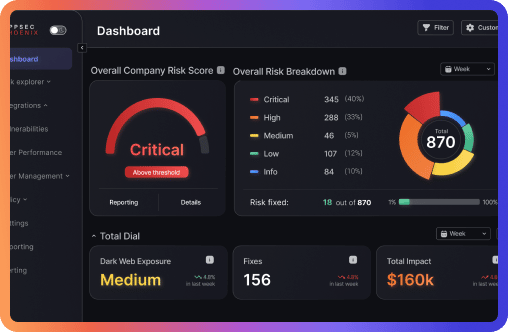
You will be able to place a threshold or target in the dashboard. As you interact with the visual data, you will be given an option to set your threshold in each of the graphs (such as in the risk progression line graph etc.) With your newly appointed threshold, you will be able to see if your application falls above or below that threshold, as well as identify where the problem areas are that are keeping that application above the threshold.
After you place your initial threshold or target and view the progression of the application’s risk over time, you will be able to adjust (override) the previous threshold to reflect any new changes in the company. For example, perhaps the new industry threshold is now lower, in which case you may override your initial threshold to reflect this change.
CVSS is an industry standard vulnerability metric. You can learn more about CVSS at FIRST.org.
Below are a few examples of vulnerabilities which may result in a given severity level. Please keep in mind that this rating does not take into account details of your installation and are to be used as a guide only.
Severity Level: Critical
Vulnerabilities that score in the critical range usually have most of the following characteristics:
For critical vulnerabilities, is advised that you patch or upgrade as soon as possible, unless you have other mitigating measures in place. For example, a mitigating factor could be if your installation is not accessible from the Internet.
Severity Level: High
Vulnerabilities that score in the high range usually have some of the following characteristics:
Severity Level: Medium
Vulnerabilities that score in the medium range usually have some of the following characteristics:
Severity Level: Low
In cybersecurity, a vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. Every organization has multiple security measures that keeps intruders out and important data in. We can think of such security measures as the fence that circumvents your yard. Vulnerabilities are cracks and openings in this fence.After exploiting a vulnerability, a cyberattack can run malicious code, install malware and even steal sensitive data.
According to the CWE/SANS Top 25 list, there are three main types of security vulnerabilities:
Software Composition Analysis (SCA), also known as Composition Analysis, is a vital aspect of application security testing. It focuses on identifying and managing the security risks associated with third-party and open-source components used in software applications. SCA tools analyze the composition of an application, including its dependencies and libraries, to detect known vulnerabilities and licensing issues. By examining the software supply chain, SCA helps organizations understand and mitigate the potential security threats posed by the components they rely on. It provides visibility into the presence of outdated or vulnerable components, enabling proactive remediation. SCA also helps ensure compliance with open-source licenses and enables organizations to track and manage the usage of third-party components effectively. By incorporating SCA into the application security testing process, organizations can bolster their defenses against security vulnerabilities introduced through the software supply chain.
References:
Static Application Security Testing (SAST) is a critical component of application security. It involves the analysis of application source code or binary files to identify potential security vulnerabilities and coding errors. SAST tools examine the code without executing it, searching for known coding patterns or security flaws that could be exploited by attackers. By detecting issues early in the development process, SAST helps developers address security concerns before the application is deployed. It helps ensure secure coding practices and improves the overall security posture of the software. SAST tools are valuable for identifying common vulnerabilities such as SQL injection, cross-site scripting (XSS), buffer overflows, and insecure cryptographic implementations. They provide insights into potential security weaknesses, enabling developers to remediate them effectively. Utilizing SAST as part of the secure software development lifecycle helps organizations build robust and secure applications.
References:
Application security tooling and orchestration refers to using specialized tools and processes to enhance the security of software applications. It systematically identifies, assesses, and mitigates security vulnerabilities and risks throughout the application development lifecycle. By implementing robust security measures and leveraging automation, organizations can protect their applications against potential threats and attacks.
The primary goal of application security tooling and orchestration is to ensure that applications are developed, deployed, and maintained with security in mind. This involves the use of various tools that aid in identifying security flaws, assessing risks, and implementing appropriate security controls. These tools can include static code analysis, dynamic application scanning, vulnerability management systems, penetration testing frameworks, and security information and event management (SIEM) solutions.
Orchestration plays a crucial role in application security by streamlining and automating security processes. It involves integrating different security tools and technologies into a cohesive workflow, enabling seamless collaboration between development, operations, and security teams. Organizations can achieve consistent and repeatable security practices through orchestration, reduce manual effort, and respond more effectively to security incidents.
Application security tooling and orchestration help organizations address a wide range of security concerns, including:
By leveraging application security tooling and orchestration, organizations can proactively identify and mitigate security risks, reduce the likelihood of successful attacks, and protect sensitive data. This approach helps foster a secure development culture and ensures that security is integral to the entire application lifecycle.
Please note that this summary provides a high-level overview of application security tooling and orchestration and may not cover all aspects in detail.
Application Security Posture Management (ASPM) is a comprehensive approach to managing and improving the overall security posture of software applications. It involves continuous monitoring, assessment, and remediation of security risks throughout the application lifecycle. ASPM solutions give organizations visibility into their applications’ security status, allowing them to identify vulnerabilities, misconfigurations, and policy violations. By leveraging automation and analytics, ASPM helps organizations proactively address security issues and prioritize remediation efforts. It enables centralized management of security policies, standards, and best practices, ensuring consistent application security across the organization. ASPM tools offer real-time insights, dashboards, and reports that facilitate risk analysis, compliance monitoring, and security posture tracking. By implementing ASPM, organizations can establish a proactive and dynamic approach to application security, effectively managing risks and maintaining a robust security posture.
References:
A website vulnerability is a weakness or misconfiguration in a website or web application code that allows an attacker to gain some level of control of the site, and possibly the hosting server. Most vulnerabilities are exploited through automated means, such as vulnerability scanners and botnets.
Most Common Website Security Vulnerabilities
Additional references
Phoenix Security allows you to specify your annualised value and divide it by the number of business applications that you run or specify the value an application generates annually.
Phoenix Security does that for you. We apply FAIR principles to derive the direct damage (current damage you could incur if an attacks happens and brings down your application or renders it unavailable) and indirect damage (remaining value of the application plus financial damage derived by brand damage, cost of the record sold on dark web, financial damage derived from Finex (e.g. GDPR)).
One of the biggest advantages of Phoenix Security is that we are able to visualize the complex data that goes behind cyber security and create a narrative that helps you understand how safe your company really is.
With the risk progression models, we are able to track the overall performance of the company’s risk over time.
Creating thresholds allows you to manage your company’s risk so that it can stay below your designated threshold. Our risk progression line graphs show the threshold you have set overlaid against the risk progression over time. This sheds light on any patterns that arise.
From the dashboard, you will be able to see the cost of your exposure over time as well as how much can be saved through fixing the exposure.
The heatmap’s ability to navigate through the most critical risks in the system is unmatched. To visually ascertain where significant risks are coming from is pivotal to understanding the nature of the vulnerability and how best to mitigate and prevent other similar risk vulnerabilities from happening.
One of the biggest advantages of Phoenix Security is that we provide our clients the ability to bring their own business logic. Phoenix security allows editing of weights for the risk formula so that every customer can specify what’s more important between:
With the risk progression models, we can track the overall performance of the company’s risk over time.
Phoenix Security supports flexible payment options. The minimum commitment is 12 months for each contract so that we can provide the best support and ongoing availability. Flexible discounts and flexible payment methods can be arranged in special cases.
Yes, you can start Phoenix security on the freemium plan then contact us to upgrade your plan to professional or enterprise at any time.
Phoenix Security offers flexible planning that allows upgrades when more assets are required. Downgrades before contract expiration are treated case by case and may involve losing history about your risk and assets.
At Phoenix Security, we pride ourselves in supporting our users and clients in every way possible, with temporary free of charge bursting capability.
You can get in touch with one of our customer representatives via the contact us form and ask at https://phoenix.security/contact/ or the webchat on the right
Kick start your journey with Phoenix Security!
Get all the guidance and answers you need on our knowledge base


Derek Fisher – Head of product security at a global fintech. Speaker, instructor, and author in application security.
Derek is an award winning author of a children’s book series in cybersecurity as well as the author of “The Application Security Handbook.” He is a university instructor at Temple University where he teaches software development security to undergraduate and graduate students. He is a speaker on topics in the cybersecurity space and has led teams, large and small, at organizations in the healthcare and financial industries. He has built and matured information security teams as well as implemented organizational information security strategies to reduce the organizations risk.
Derek got his start in the hardware engineering space where he learned about designing circuits and building assemblies for commercial and military applications. He later pursued a computer science degree in order to advance a career in software development. This is where Derek was introduced to cybersecurity and soon caught the bug. He found a mentor to help him grow in cybersecurity and then pursued a graduate degree in the subject.
Since then Derek has worked in the product security space as an architect and leader. He has led teams to deliver more secure software in organizations from multiple industries. His focus has been to raise the security awareness of the engineering organization while maintaining a practice of secure code development, delivery, and operations.
In his role, Jeevan handles a range of tasks, from architecting security solutions to collaborating with Engineering Leadership to address security vulnerabilities at scale and embed security into the fabric of the organization.

Jeevan Singh is the Director of Security Engineering at Rippling, with a background spanning various Engineering and Security leadership roles over the course of his career. He’s dedicated to the integration of security practices into software development, working to create a security-aware culture within organizations and imparting security best practices to the team.
In his role, Jeevan handles a range of tasks, from architecting security solutions to collaborating with Engineering Leadership to address security vulnerabilities at scale and embed security into the fabric of the organization.

James Berthoty has over ten years of experience across product and security domains. He founded Latio Tech to help companies find the right security tools for their needs without vendor bias.


Chris Romeo is a leading voice and thinker in application security, threat modeling, and security champions and the CEO of Devici and General Partner at Kerr Ventures. Chris hosts the award-winning “Application Security Podcast,” “The Security Table,” and “The Threat Modeling Podcast” and is a highly rated industry speaker and trainer, featured at the RSA Conference, the AppSec Village @ DefCon, OWASP Global AppSec, ISC2 Security Congress, InfoSec World and All Day DevOps. Chris founded Security Journey, a security education company, leading to an exit in 2022. Chris was the Chief Security Advocate at Cisco, spreading security knowledge through education and champion programs. Chris has twenty-six years of security experience, holding positions across the gamut, including application security, security engineering, incident response, and various Executive roles. Chris holds the CISSP and CSSLP certifications.

Jim Manico is the founder of Manicode Security, where he trains software developers on secure coding and security engineering. Jim is also the founder of Brakeman Security, Inc. and an investor/advisor for Signal Sciences. He is the author of Iron-Clad Java: Building Secure Web Applications (McGraw-Hill), a frequent speaker on secure software practices, and a member of the JavaOne Rockstar speaker community. Jim is also a volunteer for and former board member of the OWASP foundation.
Get all the latest news, exclusive deals, and feature updates.
