TOP BLOG
- 15th April 2024
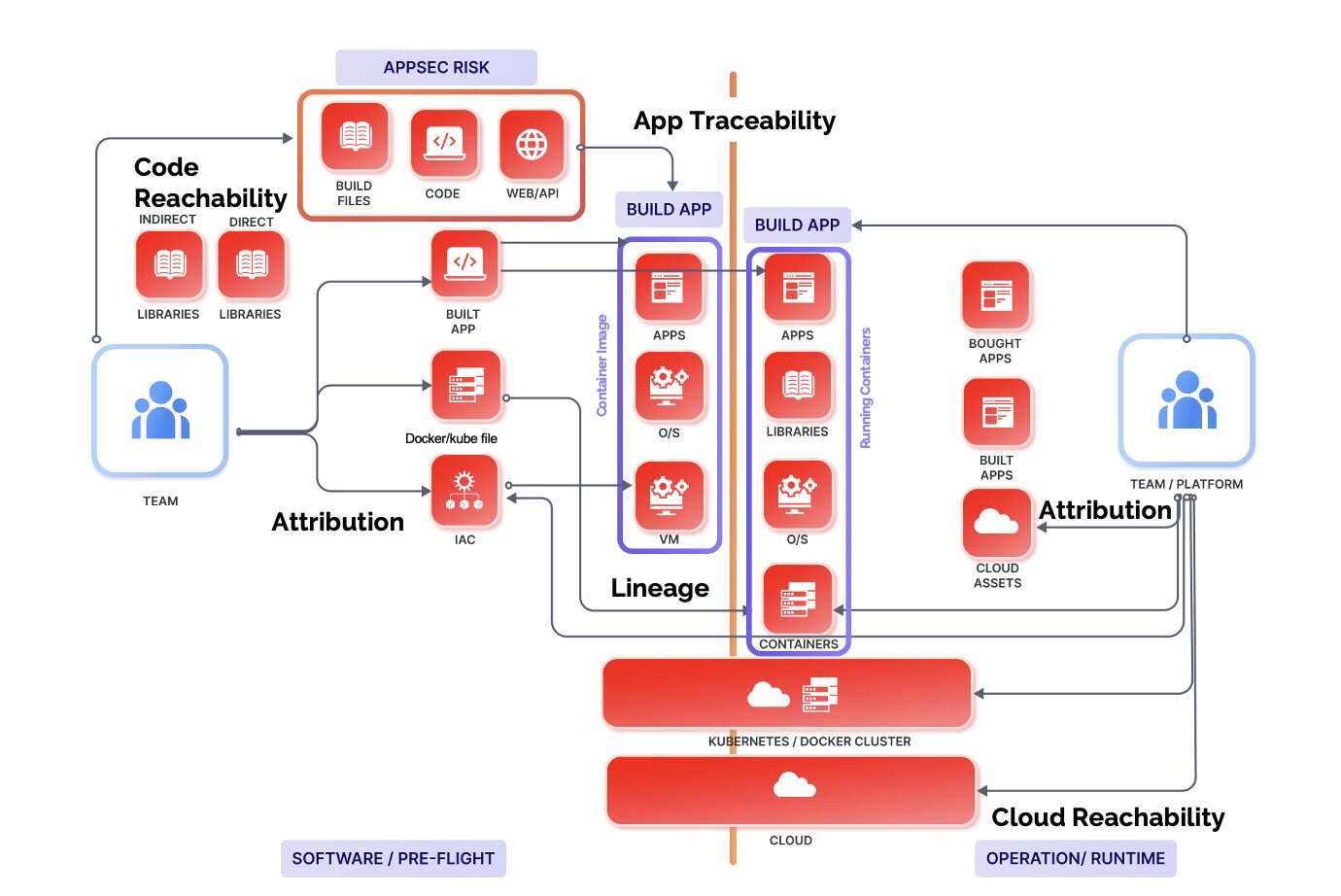
The team at Phoenix Security pleased to bring you another set of new application security (ASPM) features and improvements for vulnerability management across application and cloud security engines. This release builds on top of previous releases with key additions and progress across multiple areas of the platform. Application Security Posture Management - New Weighted Asset Risk Formula - Auto-approval of Risk Exceptions Asset and Vulnerability Management - Relative Time Filter for Vulnerabilities and Assets - Introduce "Ticket References" for Findings - Search Findings by Ticket ID - Asset Pages now have Settings "memory" Integrations - Snyk IaC+ Vulnerabilities - Extended REST API Other Improvements - Vulnerability Timeline as Stacked Lines - Display App/Env for Assigned Assets
The team at Phoenix Security pleased to bring you another set of new application security (ASPM) features and improvements for vulnerability management across application and cloud security engines. This release builds on top of previous releases with key additions and progress across multiple areas of the platform. Application Security Posture Management - New Weighted Asset Risk Formula - Auto-approval of Risk Exceptions Asset and Vulnerability Management - Relative Time Filter for Vulnerabilities and Assets - Introduce "Ticket References" for Findings - Search Findings by Ticket ID - Asset Pages now have Settings "memory" Integrations - Snyk IaC+ Vulnerabilities - Extended REST API Other Improvements - Vulnerability Timeline as Stacked Lines - Display App/Env for Assigned Assets
Alfonso Eusebio
- No Responses