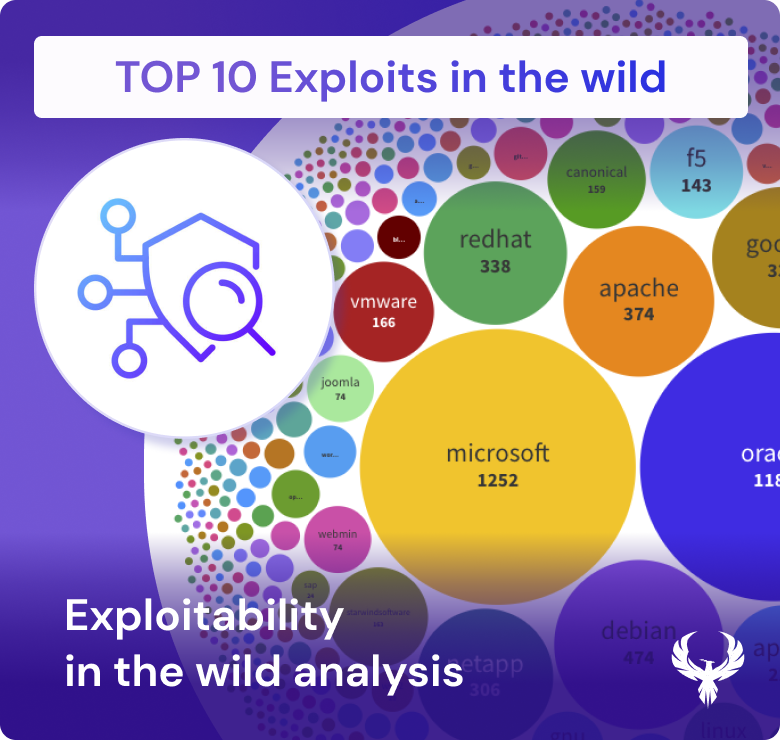
As organization look to prioritize vulnerabilitie, you should consider which vendor is more prone to explotis. As threat actors scour the digital landscape for vulnerabilities, they focus their attention on those ripe for exploitation. Here, popularity can be a double-edged sword. Exploits that gain notoriety tend to attract more attention from attackers, as they are likely to yield more significant results. This means that widely used software from vendors like Oracle, Microsoft, Red Hat, Apache, and others can become prime targets. The evidence lies in the multitude of links scattered across various sources, leading to these exploits.
These exploits, once discovered, often find their way into widely adopted vulnerability tools such as ExploitDB, MetaSploit, and Nuclei. Their accessibility through these tools amplifies their malicious potential. Moreover, the seriousness of the threat is underscored when a vulnerability achieves a high exploitation score in the Exploit Prediction Scoring System (EPSS), crossing the threshold, perhaps at 0.5 or 0.6, indicating active exploitation in the wild.
In this dynamic landscape, understanding the intricacies of exploitability, vulnerabilities, and the critical role of vulnerability management and application security is paramount. Organizations must remain vigilant, employing proactive security measures to shield their digital assets from the relentless pursuit of threat actors.