- 14th April 2024
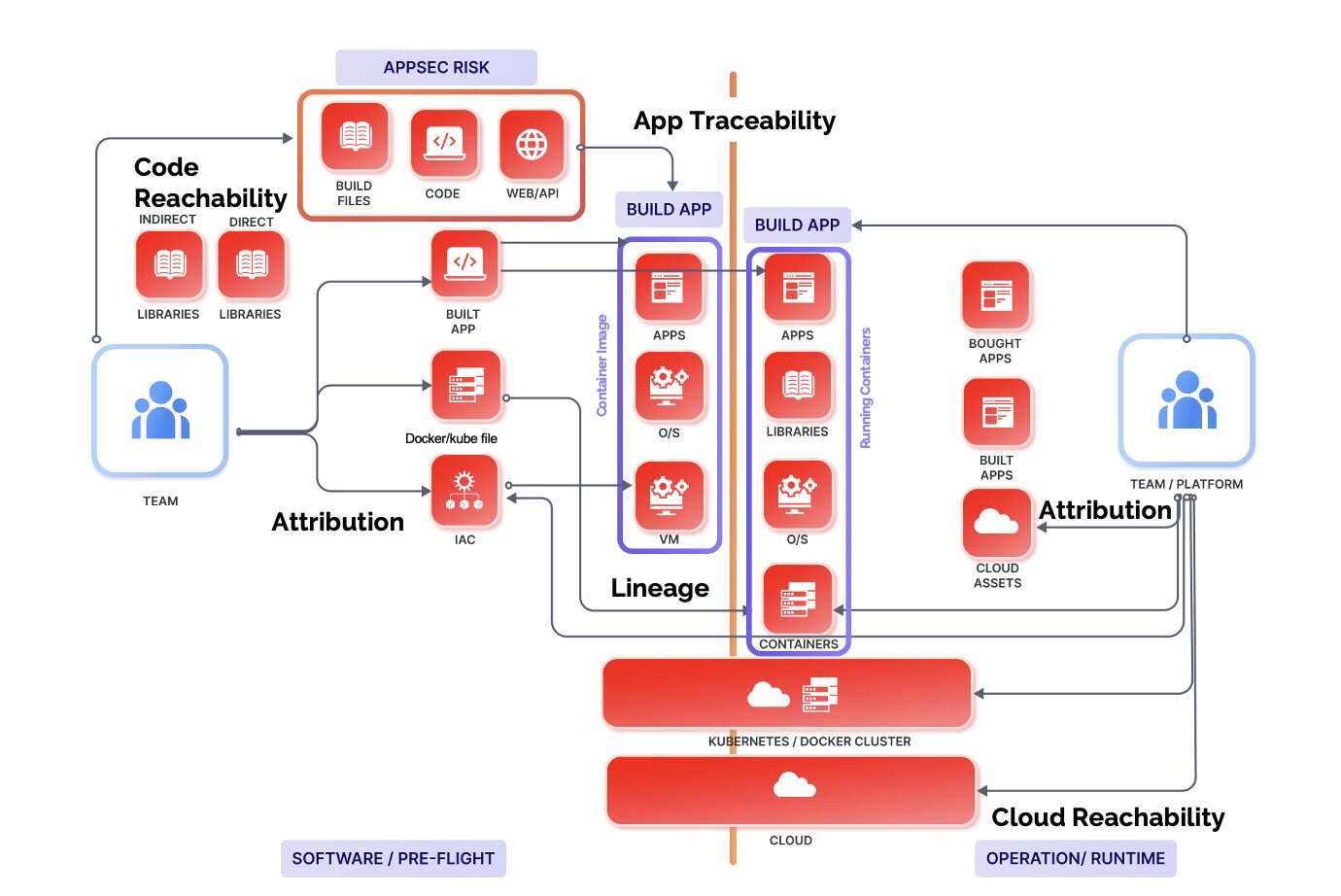
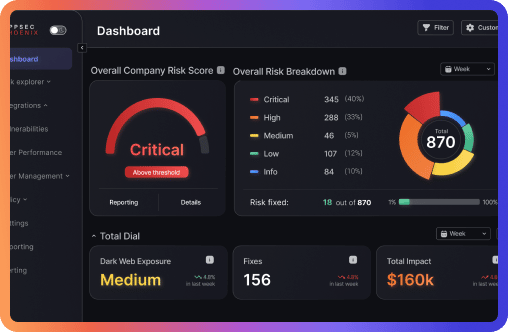
Discover and fix CVE-2024-3094 vulnerability affecting Linux distributions liblzma, part of the xz package, Fedora, openSUSE, Debian, and Kali. Get the latest updates, fixes, and security recommendations to safeguard your system against unauthorized access through compromised XZ Utils. Protect and discover the affected system with ASPM, Application security Posture management
Francesco Cipollone