TOP BLOG
- 8th August 2022
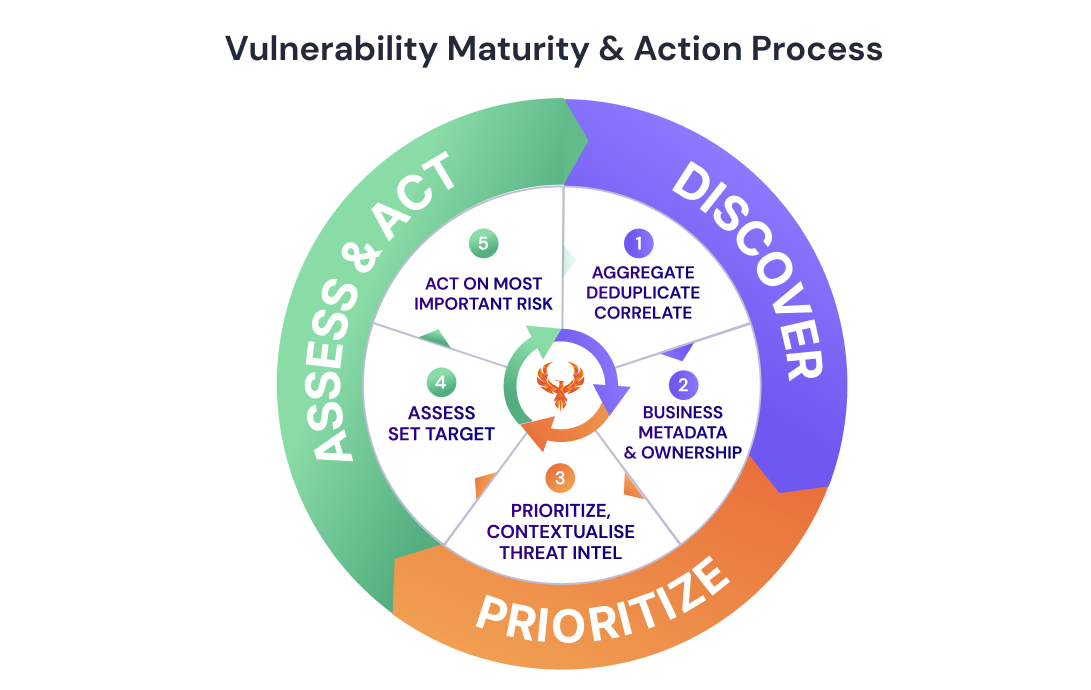
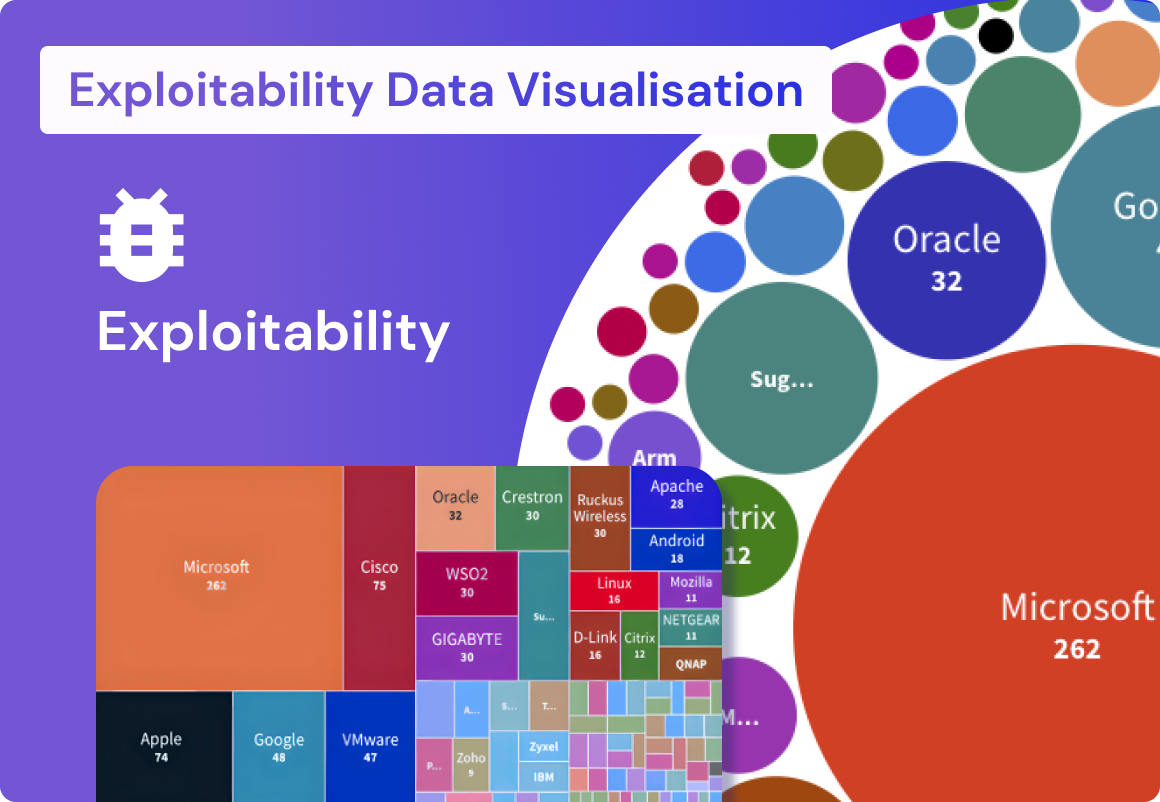
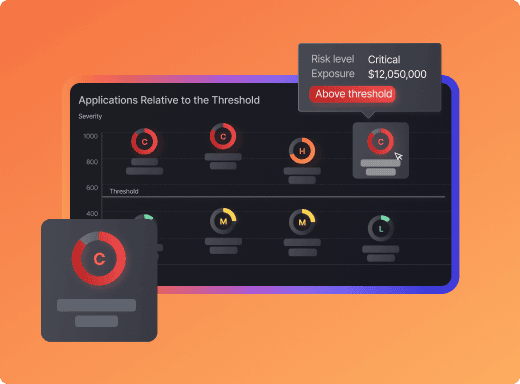
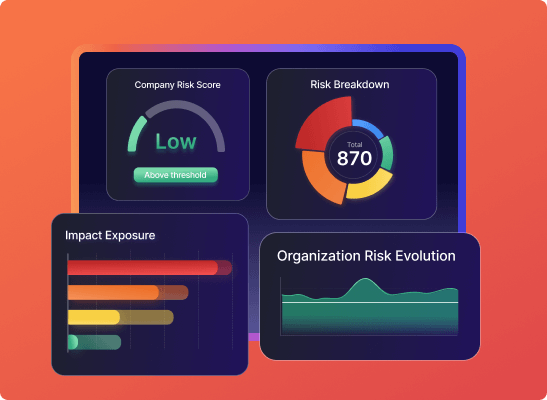
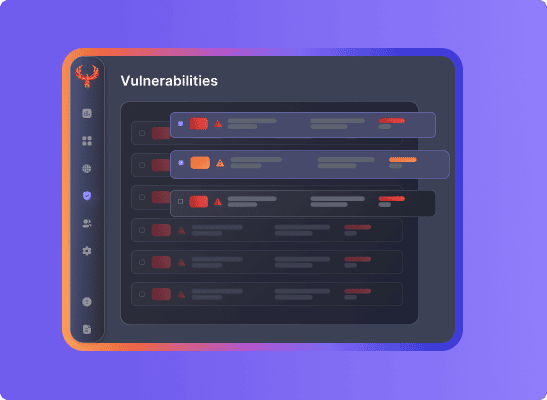
First of two part article covering Security Vulnerabilities SLA, SLO, OKr and useful tips to set objectives between development and security teams that result in reduction of risk and vulnerabilities across application security, cloud and infrastructure
First of two part article covering Security Vulnerabilities SLA, SLO, OKr and useful tips to set objectives between development and security teams that result in reduction of risk and vulnerabilities across application security, cloud and infrastructure
Francesco Cipollone
- No Responses