
“What gets measured gets managed”. William Thomson’s wisdom still rings true for cybersecurity teams in the 21st century. Effective cybersecurity protocols cannot be implemented without measuring the threats, the risks, and the potential monetary damage your business could face.
Whereas compliance-based or risk-based approaches worked in the past, the digital landscape is far too broad and alien to stakeholders today. Describing the WannaCry ransomware as a “serious risk” doesn’t help C-level executives to understand the real threat – they need a cash value to contextualize it.
Quantifying the risk that your organization faces is essential for creating an intra-company conversation that everyone understands. When the entire team can analyze, predict, and recognize new threats as they become apparent, businesses have a better chance of withstanding the stress of an attack.
Table of Contents
- Quantification For Enterprises
- The Challenges of Insuring Against Cyberattacks
- Make Quantification The Driver For Tackling Vulnerabilities
- AppSec Phoenix – How We Work
- Quantification: The InfoSec Team’s Greatest Tool
Quantification For Enterprises
Enterprises need enterprise-sized solutions. Quantification for an enterprise is necessary to contextualize the amount of risk that a cyber-attack brings – large-scale businesses have many parts, meaning that creating accessible and quantified reports gives non-specialists an insight into how vital security is for effective business operations.
One of the best ways to effectively implement cybersecurity quantification practices is by implementing the FAIR risk model into your organization and your security practices. Created by the FAIR Institue, this risk model breaks down potential threats in a way that is clear for both security professionals and non-technical stakeholders.
What is FAIR?
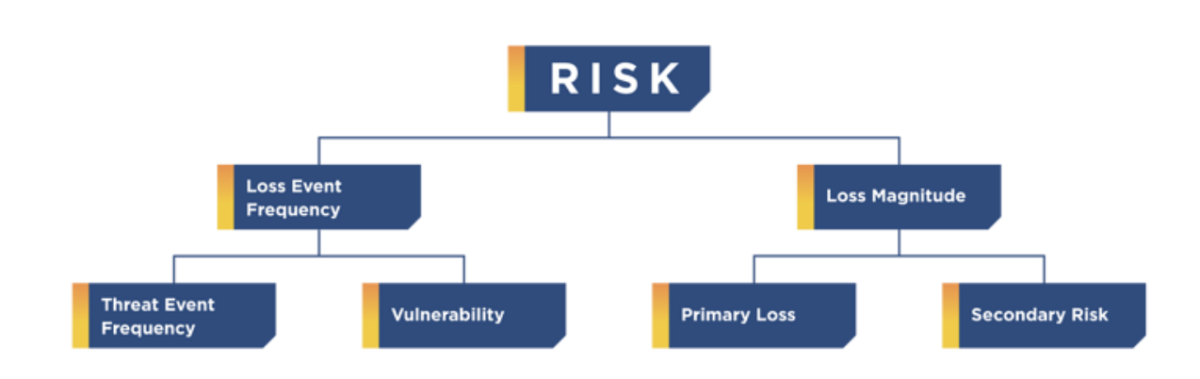
Using the FAIR risk analysis workflow to guide your decision-making process is key to developing understandable and accurate threat reports.
Source: FAIR
Factor Analysis of Information Risk (FAIR) is the only internationally recognized quantification model for analyzing cyber-risk. Reviewing information security and operational risk through the lens of FAIR brings three main benefits:
- Creating quantified measures of risk that C-level executives can understand
- Does not include vague qualitative assessment which could slow down the conversation
- Creates a foundation for full information risk management
Implementing FAIR in your security analysis workflow allows you can create intelligible reports and presentations for non-technical members of staff. FAIR is not just for creating efficient reports – it is also for creating a unified language that all stakeholders understand.
By removing qualitative “low-medium-high” risk assessments, everyone involved in the decision-making process understands the threats that the organization faces. Instead, everyone is included in an accurate assessment of lurking threats.
The Challenges of Insuring Against Cyberattacks
Quantifying cyber-security risks is not an easy task. Although 85% of security professionals carry out some sort of quantified assessment, 70% of them believe that their estimates are too conservative. This causes short-term and long-term problems for an InfoSec team.
How can we accurately estimate the amount of insurance or funding that is needed to protect an organization against cyber-crime when we can’t be sure of our estimates? There are two ways to deal with this:
- Look at how insurance companies do it, or
- Turn to analytical quantification methods
Thinking Like An Insurance Company
Insurance companies who handle cybersecurity breaches (a growing number of providers, it should be noted) break down their insurance practices into a simple formula.
The annual revenue / the number of assets = the value of the insurance
This simplistic formula then adds the likelihood of an event happening, what measures can be taken to lower the overall risk, and other factors to arrive at an acceptable level of insurance.
Although this method is basic, it provides an insight into what a quantification report needs. Identifying the necessary insurance premium (through the formula) means that we can see how much the average loss would cause the company. But is there a way to make this value more appropriate for the overall risk to the company?
Turning To Quantification
Although some might be able to pay insurance premiums based on the overall value of the company, other organizations may buckle under the weight of the potentially lofty payments. Effective quantification reports (and reacting to vulnerabilities that the reports show) are one way for cyber-security teams to lower the overall payments.
Quantification practices help security professionals to identify the actual monetary risk that an organization faces. Instead of working out the threat of an attack based on the overall revenue and number of assets, quantified risks that account for effective security measures and the steps taken to minimize allow a company to pay less.
Effective quantification doesn’t just slow the advance of malicious actors on a company’s data – companies gain the ability to plan for potential damage and build security protocols that lower insurance premiums and the overall risk.
Make Quantification The Driver For Tackling Vulnerabilities
Instead of reacting to the “malware of the month” that has struck the world, quantification needs to guide InfoSec and business decisions. Collecting data to analyze, educate, and then react appropriately can save companies from both wasteful spending on security and inadequate defenses against common threats.
The largest failing of the “low-medium-high” risk model is that, despite appearing friendlier to non-specialists, it creates a web of risks that aren’t clear. What makes one “high-risk” threat more high-risk than the next?
Driving Security Measures
Potential threats need cash values next to them. Analyzing the potential loss with the appropriate monetary risk is the best way for C-level executives (especially non-technical stakeholders) to identify changes that need to be made.
This is how one of the most frustrating areas of a security analyst’s job can become their greatest weapon. Senior executives may not understand the true extent of a cyber-security risk until it is placed in front of them alongside a cash value. Then, the security professional’s job to drive forward change and bring necessary tools and techniques into the operation is easier.
Quantification needs to drive forward change in the InfoSec department. Having a single, quantified number value for cyber-security to refer to is key – it creates structure and reason to identify and prioritize vulnerabilities and how the InfoSec team should handle them.
AppSec Phoenix and Quantification
AppSec Phoenix is not a quantification platform, but it uses similar techniques to gain meaningful information. By leveraging the business context of a threat and creating quantitative analyses to identifying the short and long-term effects, you can better understand the software you use and how it needs to be handled.
Understanding how AppSec Phoenix can change the way your organization operates is key to starting to effectively manage your security protocols. Here’s how we can improve your security and save you money at the same time.
AppSec Phoenix – How We Work
AppSec Phoenix is a unified solution to application security. Identifying and quantifying risk is already a difficult task, but we aim to simplify it by creating a single value for application cost. This cost is then associated with a variety of data that
In creating an orchestrated methodology for security scanning, mission control shows you everything you need to know – the immediacy of the risk, the full extent of risk across the system or software, and the potential monetary loss. By leveraging AI technology to identify the most immediate risks, you can have complete reports created about what risks you face and where the fightback needs to begin.
Thanks to the AppSec Phoenix aggregator, you can also manually identify what you need to do to minimize the risk of vulnerabilities. This can be a difficult process without having all the data in one place, but we calculate the direct and indirect risk levels placed upon your organization and how likely it is for an asset to become compromised.
Quantification: The InfoSec Team’s Greatest Tool
Creating a universal language that can be used for all cyber-security needs is central to quantification. For too long, cyber-threats have been misunderstood at best (or ignored at worst) because urgency and necessity are not communicated to C-level executives.
Turning focus to quantifiable, monetary losses makes quantification practices the most important tool in the security professional’s arsenal. Driving forward change is easier thanks to clear, understandable metrics which include stakeholders instead of alienating them. Hearing that you can lose $4 million instead of a vague “high-risk” warning leaves a lasting impression.
AppSec Phoenix can create reports which clearly indicate risks and how to avoid them. Using AI/ML solutions to identify the vulnerabilities that need to be handled urgently, our support is both quantified and directed. Learn the risks that your organization face, understand the extent of the potential impact, and create a plan for snuffing out the threat before it causes damage. All in one application.













