
Previous Issues of vulnerability Weekly
- Security Vulnerability of the Week 12/09/22 – Application Security – Cloud Security – Linux Malware, Windows patched 64 vulns with zero-day, Uber Hack Timeline, GTA 6/Rockstar Hack – This week we deep dive into Linux Malware, Windows patched 64 vuln with zero-day, Uber Hack Timeline, GTA 6/Rockstar Hack
- Security Vulnerability of the Week 12/09/22 – Application Security – Uber Hack Timeline – Special Focus on Uber latest news on hack
- Security Vulnerability Weekly 22/08/22 – Apple Vulnerability, Android Bugdrop Vulnerability, WordPress, CISA, and recent Hacks to Mailchimp and Twilio – Apple Vulnerability, CISA new vulnerability for September, Bugdrop new android vulnerabilities, recent hacks to twilio exposing digital ocean clients and Mailchimp hack
- Security Vulnerability of the Week 08/08/22 – Atlassian Hardcoded Credentials, Sonicwall GSM, Cisco Nexus, Microsoft Macro, Vmware Fix, Mac OS spotlight vulnerability and more
- Security Vulnerability of the Week 25/07/22– Atlassian Hardcoded Credentials, Sonicwall GSM, Cisco Nexus, Microsoft Macro, Vmware Fix, Mac OS spotlight vulnerability and more
- Security Vulnerability of the Week 10/07/22 – OPENSSL Hearbleed2, Apache Common, CuteBoi NPM exploit, Iconburst NPM exploit, Orbit attack, Follina Weaponization, Chrome’s latest vulnerabilities
- Security Vulnerability of the Week 04/07/22 – Jenkins massive plugins issue , zoho, Exchange backdoors, Edge high vuln
This week we focus on the zero-day release on the 29 with a detailed analysis of the attacks and results so far in mitigations.
Two new Microsoft Exchange zero-days exploited in the wild from Chinese ATP
On September 30th, two vulnerabilities were discovered in a large attack.
On September 29, a Vietnamese researcher warned the ATP was targeting exchange servers with RCE directly on the system.
As RCE is a category of devastating attacks as they allow an attacker to further deploy payloads and additional exploits.
GTSC suspects that a Chinese threat group is responsible for the attacks based on the web shells’ code page, a Microsoft character encoding for simplified Chinese.
“The vulnerability turns out to be so critical that it allows the attacker to do RCE on the compromised system,” the researchers said.
Name
Proxy no shell is from the researcher Kevin Beaumont named the vulnerabilities ProxyNotShell due to similarities to the Exchange vulnerability dubbed ProxyShell, which has been exploited in the wild for more than a year. Microsoft’s patches for ProxyShell do not completely remove an attack vector.
The researchers reported the security vulnerabilities to Microsoft three weeks ago through the Zero Day Initiative, which tracks them as ZDI-CAN-18333 and ZDI-CAN-18802 after its analysts validated the issues.
GTSC has released very few details regarding these zero-day bugs. Still, its researchers did reveal that the requests used in this exploit chain are similar to those used in attacks targeting the ProxyShell vulnerabilities.
The exploit works in two stages:
- Requests with a similar format to the ProxyShell vulnerability: autodiscover/autodiscover.json?@evil.com/<Exchange-backend-endpoint>&Email=autodiscover/autodiscover.json%3f@evil.com.
- The use of the link above to access a component in the backend where the RCE could be implemented.
“The version number of these Exchange servers showed that the latest update had already installed, so an exploitation using Proxyshell vulnerability was impossible,” the researchers said.
Admins who want to check if their Exchange servers have already been compromised using this exploit can run the following PowerShell command to scan IIS log files for indicators of compromise:
Get-ChildItem -Recurse -Path <Path_IIS_Logs> -Filter “*.log” | Select-String -Pattern ‘powershell.*autodiscover.json.*@.*200’
For full malware analysis: https://gteltsc.vn/blog/warning-new-attack-campaign-utilized-a-new-0day-rce-vulnerability-on-microsoft-exchange-server-12715.html
Detail of the attack and chain

” MSTIC observed activity related to a single activity group in August 2022 that achieved initial access and compromised Exchange servers by chaining CVE-2022-41040 and CVE-2022-41082 in a small number of targeted attacks. These attacks installed the Chopper web shell to facilitate hands-on-keyboard access, which the attackers used to perform Active Directory reconnaissance and data exfiltration. Microsoft observed these attacks in fewer than 10 organizations globally. MSTIC assesses with medium confidence that the single activity group is likely to be a state-sponsored organization.”
After the discovery two Zero day initiative vulnerabilities were recorded:
Microsoft issued the statement:
Microsoft is investigating two reported zero-day vulnerabilities affecting Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. The first one, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, and the second one, identified as CVE-2022-41082, allows Remote Code Execution (RCE) when PowerShell is accessible to the attacker.
Microsoft has recently published
Mitigation:
— exploits
While details have not been made public for the vulnerabilities in order to prevent abuse, some individuals have been offering ProxyNotShell proof-of-concept (PoC) exploits that have turned out to be fake.
— Detection
Some members of the cybersecurity community have released open source tools that can be used to detect the presence of vulnerabilities.
One example is: https://twitter.com/q8fawazo/status/1576503359359832064
Mitigation update
Important updates have been made to the Mitigations section improving the URL Rewrite rule. Customers should review the Mitigations section and apply one of these updated mitigation options:
- Option 1: The EEMS rule is updated and is automatically applied.
- Option 2: The previously provided EOMTv2 script has been updated to include the URL Rewrite improvement.
- Option 3: The URL Rewrite rule instructions have been updated. The string in step 6 and step 9 has been revised. Steps 8, 9, and 10 have updated images.
- Updated Detection section to refer to Analyzing attacks using the Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082.
Online Exchange
Alert as highly exploitable (especially 41040). The current Exchange Server mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> URL Rewrite -> Actions” to block the known attack patterns
On-premises exchange:
“The current mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> Autodiscover -> URL Rewrite -> Actions” to block the known attack patterns.”
To apply the mitigation to vulnerable servers, you will need to go through the following steps:
- Open the IIS Manager.
- Expand the Default Web Site.
- Select Autodiscover.
- In the Feature View, click URL Rewrite.
- In the Actions pane on the right-hand side, click Add Rules.
- Select Request Blocking and click OK.
- Add String “.*autodiscover.json.*@.*Powershell.*” (excluding quotes) and click OK.
- Expand the rule and select the rule with the Pattern “.*autodiscover.json.*@.*Powershell.*” and click Edit under Conditions.
- Change the condition input from {URL} to {REQUEST_URI}
Since the threat actors can also gain access to PowerShell Remoting on exposed and vulnerable Exchange servers for remote code execution via CVE-2022-41082 exploitation, Microsoft also advises admins to block the following Remote PowerShell ports to hinder the attacks:
- HTTP: 5985
- HTTPS: 5986
On-premises exchange, follow the recommendations: https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
Option 2: Microsoft created the following script for the URL Rewrite mitigation steps. https://aka.ms/EOMTv2
Detection
Phoenix Security

We made available for all the users free and not the Alerting system to select the assets and vulnerability automatically to solve

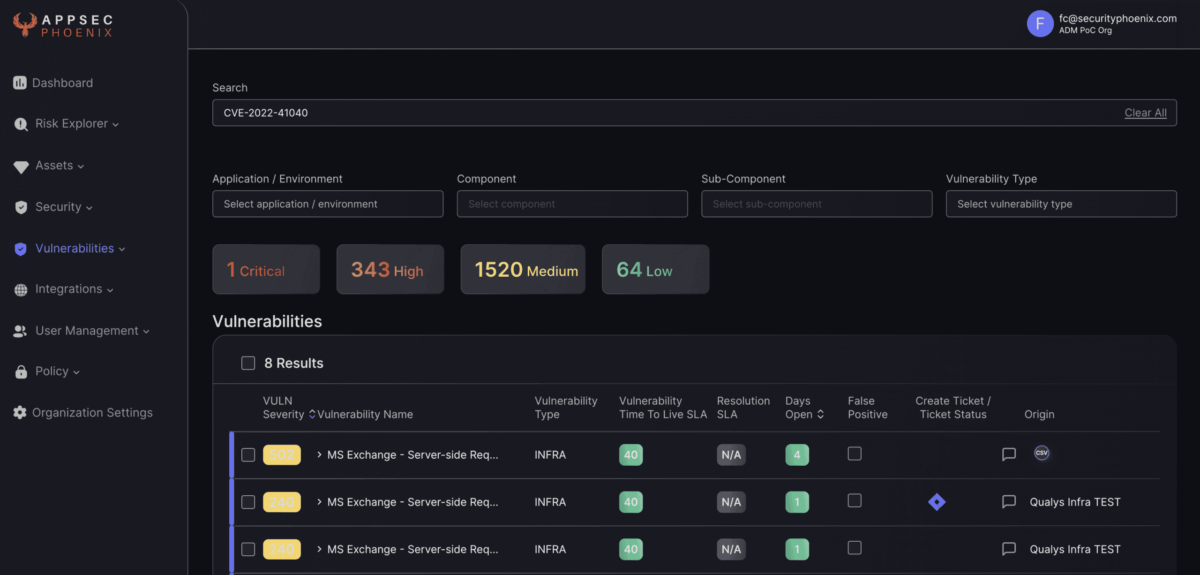

Get access today to the community edition using the link below for free. If you need more assets to scan, we will be happy to help you and provide more licence for free during these challenging times
Post exploitation detection/IoC
Filenames linked to the post-exploitation (see below section for a full hunting suite section)
| FileName | Path |
| RedirSuiteServiceProxy.aspx | C:ProgramFilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauth |
| Xml.ashx | C:inetpubwwwrootaspnet_client |
| pxh4HG1v.ashx | C:ProgramFilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauth |

Suspicious File
On the servers, we detected suspicious files of exe and dll formats
| FileName | Path |
| DrSDKCaller.exe | C:rootDrSDKCaller.exe |
| all.exe | C:UsersPublicall.exe |
| dump.dll | C:UsersPublicdump.dll |
| ad.exe | C:UsersPublicad.exe |
| gpg-error.exe | C:PerfLogsgpg-error.exe |
| cm.exe | C:PerfLogscm.exe |
| msado32.tlb | C:Program FilesCommon Filessystemadomsado32.tlb |
Microsoft Exchange Web attack Surface & Attack path
Currently, there are 318382 exchange servers exposed over the public web, all of them could potentially be a target for this new zero-day
At the time of the attack USA, Japan, and UK/Germany were the targets of ATP coming from China.
Detection of compromise Hunting Queries:
Currently, Microsoft has released a full detailed GitHub repository to detect compromises
https://github.com/microsoft/CSS-Exchange/tree/main/Security
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint detects post-exploitation activity. The following alerts could be related to this thread:
| Indicators of attack | MITRE ATT&CK techniques observed |
| Possible web shell installation | Installation |
| Possible IIS web shell | Installation |
| Suspicious Exchange Process Execution | Actions |
| Possible exploitation of Exchange Server vulnerabilities (Requires Exchange AMSI to be enabled) | Exploitation |
| Suspicious processes indicative of a web shell | Actions |
| Possible IIS compromise | Actions |
Microsoft Sentinel
Based on what we’re seeing in the wild, Microsoft Sentinel customers can use the following techniques for web shell-related attacks connected to these vulnerabilities. Our post on web shell threat hunting with Microsoft Sentinel also provides general guidance on looking for web shells.
The Exchange SSRF Autodiscover ProxyShell detection, created in response to ProxyShell, can be used for queries due to functional similarities with this threat. Also, the new Exchange Server Suspicious File Downloads and Exchange Worker Process Making Remote Call queries look for suspicious downloads or activity in IIS logs. In addition to these, we have a few more that could be helpful in looking for post-exploitation activities:
Microsoft 365 Defender
Use this query to hunt for Chopper web shell activity:
DeviceProcessEvents
| where InitiatingProcessFileName =~ "w3wp.exe"
| where ProcessCommandLine has_any ("&ipconfig&echo", "&quser&echo", "&whoami&echo", "&c:&echo", "&cd&echo", "&dir&echo", "&echo [E]", "&echo [S]")
Suspicious files in Exchange directories
Use this query to hunt for suspicious files in Exchange directories:
DeviceFileEvents | where Timestamp >= ago(7d) | where InitiatingProcessFileName == "w3wp.exe" | where FolderPath has "FrontEnd\HttpProxy\" | where InitiatingProcessCommandLine contains "MSExchange" | project FileName,FolderPath,SHA256, InitiatingProcessCommandLine, DeviceId, Timestamp
Details on the vulnerabilities
CVE-2022-41040, is a Server-Side Request Forgery (SSRF) –
A vulnerability has been found in Microsoft Exchange Server 2013/2016/2019 and classified as critical. This vulnerability affects an unknown part. The manipulation with an unknown input leads to a privilege escalation vulnerability. The CWE definition for vulnerability is CWE-918. The web server receives a URL or similar request from an upstream component and retrieves the contents of this URL, but it does not sufficiently ensure that the request is being sent to the expected destination. As an impact it is known to affect confidentiality, integrity, and availability.
The weakness was published on 09/30/2022. The advisory is available at msrc-blog.microsoft.com. This vulnerability was named CVE-2022-41040. Technical details are unknown but an exploit is available.
The structure of the vulnerability defines a possible price range of USD $5k-$25k at the moment (estimation from vulndb) even tough exploit was developed by
It is declared as highly functional.
It is possible to mitigate the problem by applying the configuration setting.
Why EPSS alone was not active – EPSS currently is scoring vulnerabilities at 0.0 (data still needs to be retrieved)
CTI information gives a range from 8 to now 5 after successful mitigation
CVE-2022-41082– Microsoft Advisory
Currently actively exploited in the wild with persistence – exploit is less active than CVE-2022-41040,
A vulnerability was found in Microsoft Exchange Server 2013/2016/2019 and classified as critical. This issue affects an unknown code of the component PowerShell Handler. Impacted is confidentiality, integrity, and availability.
The weakness was released on 09/30/2022. It is possible to read the advisory at msrc-blog.microsoft.com. The identification of this vulnerability is CVE-2022-41082. Technical details are unknown but an exploit is available. The pricing for an exploit might be around USD $5k-$25k at the moment (estimation from vulndb).
Indicators of Compromise (IOCs)
Webshell:
File Name: pxh4HG1v.ashx
Hash (SHA256): c838e77afe750d713e67ffeb4ec1b82ee9066cbe21f11181fd34429f70831ec1
Path: C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthpxh4HG1v.ashx
File Name: RedirSuiteServiceProxy.aspx
Hash (SHA256): 65a002fe655dc1751add167cf00adf284c080ab2e97cd386881518d3a31d27f5
Path: C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthRedirSuiteServiceProxy.aspx
File Name: RedirSuiteServiceProxy.aspx
Hash (SHA256): b5038f1912e7253c7747d2f0fa5310ee8319288f818392298fd92009926268ca
Path: C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthRedirSuiteServiceProxy.aspx
File Name: Xml.ashx (pxh4HG1v.ashx and Xml.ashx, 2 files have the same contents)
Hash (SHA256): c838e77afe750d713e67ffeb4ec1b82ee9066cbe21f11181fd34429f70831ec1
Path: C:inetpubwwwrootaspnet_clientXml.ashx
Filename: errorEE.aspx
SHA256: be07bd9310d7a487ca2f49bcdaafb9513c0c8f99921fdf79a05eaba25b52d257
Path: C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaautherrorEE.aspx
DLL:
File name: Dll.dll
SHA256:
074eb0e75bb2d8f59f1fd571a8c5b76f9c899834893da6f7591b68531f2b5d82
45c8233236a69a081ee390d4faa253177180b2bd45d8ed08369e07429ffbe0a9
9ceca98c2b24ee30d64184d9d2470f6f2509ed914dafb87604123057a14c57c0
29b75f0db3006440651c6342dc3c0672210cfb339141c75e12f6c84d990931c3
c8c907a67955bcdf07dd11d35f2a23498fb5ffe5c6b5d7f36870cf07da47bff2
File name: 180000000.dll (Dump từ tiến trình Svchost.exe)
SHA256: 76a2f2644cb372f540e179ca2baa110b71de3370bb560aca65dcddbd7da3701e
IP:
125[.]212[.]220[.]48
5[.]180[.]61[.]17
47[.]242[.]39[.]92
61[.]244[.]94[.]85
86[.]48[.]6[.]69
86[.]48[.]12[.]64
94[.]140[.]8[.]48
94[.]140[.]8[.]113
103[.]9[.]76[.]208
103[.]9[.]76[.]211
104[.]244[.]79[.]6
112[.]118[.]48[.]186
122[.]155[.]174[.]188
125[.]212[.]241[.]134
185[.]220[.]101[.]182
194[.]150[.]167[.]88
212[.]119[.]34[.]11
URL:
hxxp://206[.]188[.]196[.]77:8080/themes.aspx
C2:
137[.]184[.]67[.]33
- Security Vulnerability of the Week 12/09/22 – Application Security – Cloud Security – Linux Malware, Windows patched 64 vulns with zero-day, Uber Hack Timeline, GTA 6/Rockstar Hack – This week we deep dive into Linux Malware, Windows patched 64 vuln with zero-day, Uber Hack Timeline, GTA 6/Rockstar Hack
- Security Vulnerability of the Week 12/09/22 – Application Security – Uber Hack Timeline – Special Focus on Uber latest news on hack
- Security Vulnerability Weekly 22/08/22 – Apple Vulnerability, Android Bugdrop Vulnerability, WordPress, CISA, and recent Hacks to Mailchimp and Twilio – Apple Vulnerability, CISA new vulnerability for September, Bugdrop new android vulnerabilities, recent hacks to Twilio exposing digital ocaean clients and Mailchimp hack
- Security Vulnerability of the Week 08/08/22 – Atlassian Hardcoded Credentials, Sonicwall GSM, Cisco Nexus, Microsoft Macro, Vmware Fix, Mac OS spotlight vulnerability and more
- Security Vulnerability of the Week 25/07/22– Atlassian Hardcoded Credentials, Sonicwall GSM, Cisco Nexus, Microsoft Macro, Vmware Fix, Mac OS spotlight vulnerability and more
- Security Vulnerability of the Week 10/07/22 – OPENSSL Hearbleed2, Apache Common, CuteBoi NPM exploit, Iconburst NPM exploit, Orbit attack, Follina Weaponization, Chrome’s latest vulnerabilities
- Security Vulnerability of the Week 04/07/22 – Jenkins massive plugins issue , zoho, Exchange backdoors, Edge high vuln














